Ibsurgeon First Aid Crack

Like said by Mark, it is not that the database 'does not have SYSDBA user' - databases in Firebird 2.x never have users - but that old trick was used to create SYSDBA named role in order to trigger names collision on login. After scanning through I have two suggestions for you. • You can try some tool that opens Firebird databases without using Firebird itself to learn with username can pull you out of the deadlock. One such tool is Database Explorer in the IBExpert.
Full IBExpert is paid for non-USSR states and free IBExpert Personal probably does not have the tool. But I hope the tool works in IBExpert Trial. Another tool is IBSurgeon FirstAID. And probably there are more tools featuring data extraction from corrupt databases.
IBSurgeon is glad to announce the new version of Firebird and InterBase database recovery tool: FirstAID 3.7.
Feedback in Amplifiers 13. Switching Circuits (Multi-vibrators) 16. Sinusoidal Oscillators 15. Power Amplifiers 14. Small Signal Amplifiers 12. Electronic devices and circuits by sanjeev gupta pdf to word.
You only need to find and read one specific row. The query to create the blocking role is given on the 23rd page of the presentation.
INSERT INTO RDB$ROLES(RDB$ROLE_NAME, RDB$OWNER_NAME) VALUES (‘SYSDBA’, ‘LOCKSMITH’); So you would have to look into the said table, find the row with the said role, and learn the username that has authority over that role (in the example it was LOCKSMITH). After that you connect to any other database on the same server and you create the user with the name you learnt. Then you use that name to login into the problematic database and to DROP ROLE SYSDBA; COMMIT.
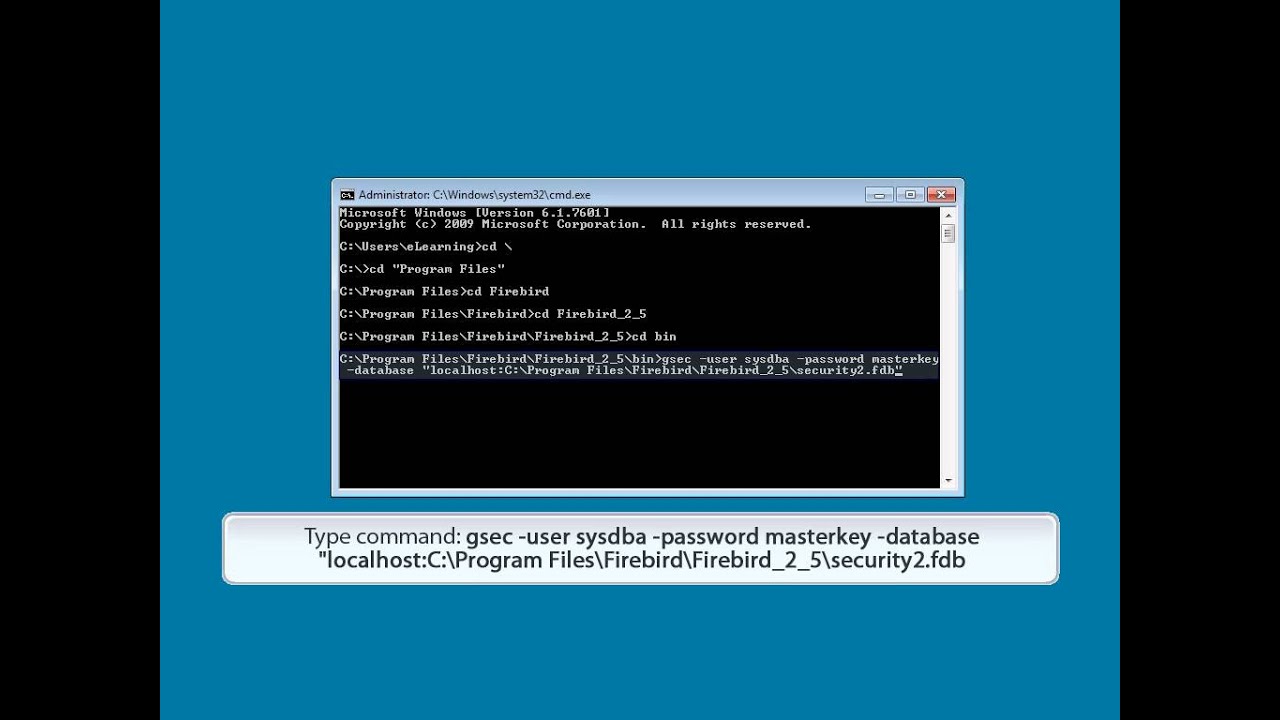
• You also can use Firebird Embedded. All server-coded security checks are bypassed in the Embedded edition of FB 2.x (but if DB designer added some ad hoc security checks in triggers - they will work).
Hp ewa keygen download for windows. So you login into the problematic database using Firebird Embedded edition, any username and any password, and after that you drop the access blocking role.
Tuesday, Jan. 28 Senate Intelligence — 9:30 a.m. — 216 Hart Worldwide threats The heads of the FBI, CIA, DIA and NSA will testify before the committee on national security threats facing the country. Senate Homeland Security — 10 a.m.
— 342 Dirksen Organizational meeting The committee will hold its first meeting of the year, to formally approve new rules and subcommittee assignments. Senate Armed Services — 10 a.m. — G50 Dirksen China and Russia Outside experts will testify before the committee on military and security threats posed by China and Russia.
House Armed Services — 10 a.m. — 2118 Rayburn Southern border deployments Committee members will look at the ongoing deployment of active-duty troops to the southern U.S.
Border and the effects on military readiness. Senate Armed Services — 2:30 p.m. — 222 Russell DOD cybersecurity Pentagon officials will testify before the committee on department cybersecurity policies and architecture. Thursday, Jan. 31 House Oversight — 10 a.m. — 2154 Rayburn Coast Guard Committee members will look at the impact of the ongoing government shutdown on the Coast Guard.